I2P Router Help
¿Sobre qué sistemas funcionará I2P?
I2P is written in the Java programming language. It has been tested on Windows, Linux, FreeBSD and OSX. An Android port is also available.
In terms of memory usage, I2P is configured to use 128 MB of RAM by default. This is sufficient for browsing and IRC usage. However, other activities may require greater memory allocation. For example, if one wishes to run a high-bandwidth router, participate in I2P torrents or serve high-traffic hidden services, a higher amount of memory is required.
In terms of CPU usage, I2P has been tested to run on modest systems such as the Raspberry Pi range of single-board computers. As I2P makes heavy use of cryptographic techniques, a stronger CPU will be better suited to handle the workload generated by I2P as well as tasks related to the rest of the system (i.e. Operating System, GUI, Other processes e.g. Web Browsing).
A comparison of some of the available Java Runtime Environments (JRE) is available here: https://trac.i2p2.de/wiki/java. Using Sun/Oracle Java or OpenJDK is recommended.
¿Se requiere instalar Java para usar I2P?
Aunque la principal implementación de cliente I2P requiere Java, hay varios clientes alternativos que no requieren Java.
What is an "I2P Site?"
Formerly called an eepSite, an I2P Site is a website that is hosted anonymously, a hidden service which is accessible through your web browser. It can be accessed by setting your web browser's HTTP proxy to use the I2P web proxy (typically it listens on localhost port 4444), and browsing to the site. Detailed instructions for configuring your browse can be found on the browser configuration page.
¿Qué significan los números activos x/y en la consola del router?
x is the number of peers you've sent or received a message from successfully in the last minute, y is the number of peers seen in the last hour or so. Try hovering your cursor over the other lines of information for a brief description.
Estoy en contra de ciertos tipos de contenido. ¿Cómo evito almacenarlos, distribuirlos o acceder a ellos?
I2P traffic that transits through your router is encrypted with several layers of encryption. Except in the case of a serious security vulnerability (of which none are currently known), it is not possible to know the content, origin or destination of routed traffic.
-
Distribution
All traffic on the I2P network is encrypted in multiple layers. You don't know a message's contents, source, or destination. Traffic is internal to the I2P network, you are not an exit node (referred to as an outproxy in our documentation). -
Storage
The I2P network does not do distributed storage of content, this has to be specifically installed and configured by the user (with Tahoe-LAFS, for example). That is a feature of a different anonymous network, Freenet. By running an I2P router, you are not storing content for anyone. -
Access
Your router will not request any content without your specific instruction to do so.
Is it possible to block I2P?
Sí, con mucho, la forma más fácil y más común es mediante el bloqueo de bootstrap, o "Reseed" de servidores. Bloquear completamente todo el tráfico ofuscado también funcionaría (aunque rompería muchas, muchas otras cosas que no son I2P y la mayoría no están dispuestos a ir tan lejos). En el caso del bloqueo de reseed, hay un paquete de reseed en Github, bloquearlo también bloqueará Github. Puedes hacer reseed a través de un proxy (se pueden encontrar muchos en Internet si no quieres usar Tor) o compartir paquetes de reseed de amigo a amigo sin conexión.
En el archivo wrapper.log veo un error que indica "Protocol family unavailable" cuando arranco la consola del ruter.
A menudo este error ocurre con cualquier aplicación java que active la red en sistemas configurados para usar IPV6 por defecto. Hay varias formas de arreglarlo:
-
En sistemas basados en Linux puede ejecutar
echo 0 > /proc/sys/net/ipv6/bindv6only - Busque por las siguientes líneas en
wrapper.config.
#wrapper.java.additional.5=-Djava.net.preferIPv4Stack=true
#wrapper.java.additional.6=-Djava.net.preferIPv6Addresses=false
Si las líneas ya están ahí, descomentelas eliminando los "#". Si las líneas no están ahí añádalas sin los "#".
~/.i2p/clients.config
CUIDADO: Para que los cambios en wrapper.config tengan efecto debe apagar completamente el ruter y el wrapper. ¡Pulsando Reiniciar en la consola del ruter NO leerá de nuevo este archivo! Tiene que pulsar apagar, esperar 11 minutos y entonces arrancar I2P.
¿La mayoría de los sitios de I2P no funcionan?
If you consider every I2P Site that has ever been created, yes, most of them are down. People and I2P Sites come and go. A good way to get started in I2P is check out a list of I2P Sites that are currently up. http://identiguy.i2p.xyz tracks active I2P Sites.
¿Porqué está escuchando I2P en el puerto 32000?
El Tanuki java service wrapper que utilizamos abre este puerto —vinculado a localhost— con el fin de comunicarse con el software que se ejecuta dentro de la JVM. Cuando se lanza la JVM se le da una clave para que pueda conectarse a la envoltura. Después de que la JVM establece su conexión con la envoltura, ésta rechaza cualquier conexión adicional.
Encontrará más información en la documentación sobre envoltorios.
Configuration
¿Cómo configuro mi navegador web?
The proxy config for different browsers is on a separate page with screenshots. More advanced configs with external tools, such as the browser plug-in FoxyProxy or the proxy server Privoxy, are possible but could introduce leaks in your setup.
¿Cómo conecto a un IRC dentro de I2P?
A tunnel to the main IRC server within I2P, Irc2P, is created when I2P is installed (see the I2PTunnel configuration page), and is automatically started when the I2P router starts.
To connect to it, tell your IRC client to connect to localhost 6668.
HexChat-like client users can create a new network with the server localhost/6668 (remember to tick "Bypass proxy server" if you have a proxy server configured).
Weechat users can use the following command to add a new network:
/server add irc2p localhost/6668
¿Cómo puedo crear mi propio sitio I2P?
Pulse en el enlace a la página web en la parte de arriba de las instrucciones de la consola del ruter.
Si alojo un sitio web en I2P en casa, que sólo contenga HTML y CSS, ¿es peligroso?
Si alojas un blog personal o haces algo que no sea sensible, obviamente corres poco peligro. Si tienes necesidades de privacidad que básicamente no son específicas, corres poco peligro. Si estás alojando algo sensible, entonces tus servicios se caerán al mismo tiempo que tu router. Alguien que observe su tiempo de inactividad y lo correlacione con eventos del mundo real probablemente podría desanonimizarte con suficiente esfuerzo. I2P tiene defensas disponibles contra esto como multihoming o Tahoe-LAFS, pero requieren una configuración adicional y sólo son apropiadas para algunos modelos de amenaza. No existe una solución mágica. protegerse de una amenaza real requerirá una consideración real en cualquier caso.
¿Cómo encuentra I2P los sitios web ".i2p"?
The I2P Address Book application maps human-readable names to long-term destinations, associated with services, making it more like a hosts file or a contact list than a network database or a DNS service. It's also local-first there is no recognized global namespace, you decide what any given .i2p domain maps to in the end. The middle-ground is something called a "Jump Service" which provides a human-readable name by redirecting you to a page where you will be asked "Do you give the I2P router permission to call $SITE_CRYPTO_KEY the name $SITE_NAME.i2p" or something to that effect. Once it's in your address book, you can generate your own jump URL's to help share the site with others.
¿Cómo añado direcciones a la Agenda?
No puede añadir una dirección sin conocer al menos el base32 o el base64 del sitio que desea visitar. El "nombre de host" que es legible por humanos es sólo un alias para la dirección criptográfica, que corresponde a base32 o base64. Sin la dirección criptográfica, no hay manera de acceder a un sitio I2P, esto es por diseño. Distribuir la dirección a las personas que aún no la conocen suele ser responsabilidad del proveedor del servicio Jump. Visitar un Sitio I2P que es desconocido activará el uso de un servicio Jump. stats.i2p es el servicio Jump más fiable.
Si estás alojando un sitio a través de i2ptunnel, entonces todavía no tendrá un registro con un servicio de salto. Para darle una URL localmente, entonces visita la página de configuración y haz clic en el botón que dice "Añadir a la libreta de direcciones local". A continuación, vaya a http://127.0.0.1:7657/dns para buscar la URL de addresshelper y compártala.
¿Qué puertos usa I2P?
Los puertos que utiliza I2P pueden dividirse en 2 secciones:
- Puertos orientados a Internet, que se utilizan para la comunicación con otros routers I2P
- Puertos locales, para conexiones locales
A continuación se describen detalladamente.
- Internet-facing ports
Note: Since release 0.7.8, new installs do not use port 8887; a random port between 9000 and 31000 is selected when the program is run for the first time. The selected port is shown on the router configuration page.
OUTBOUND- UDP from the random port listed on the configuration page to arbitrary remote UDP ports, allowing for replies
- TCP from random high ports to arbitrary remote TCP ports
- Outbound UDP on port 123, allowing for replies. This is necessary for I2P's internal time sync (via SNTP - querying a random SNTP host in pool.ntp.org or another server you specify)
- (Optional, recommended) UDP to the port noted on the configuration page from arbitrary locations
- (Optional, recommended) TCP to the port noted on configuration page from arbitrary locations
- Inbound TCP can be disabled on the configuration page
- Local I2P ports, listening only to local connections by default, except where noted:
PORT PURPOSE DESCRIPCIÓN 1900 UPnP SSDP UDP multicast listener Cannot be changed. Binds to all interfaces. May be disabled on confignet. 2827 BOB bridge A higher level socket API for clients. Disabled by default. May be enabled/disabled on configclients. May be changed in the bob.config file. 4444 HTTP proxy May be disabled or changed on the i2ptunnel page in the router console. May also be configured to be bound to a specific interface or all interfaces. 4445 HTTPS proxy May be disabled or changed on the i2ptunnel page in the router console. May also be configured to be bound to a specific interface or all interfaces. 6668 IRC proxy May be disabled or changed on the i2ptunnel page in the router console. May also be configured to be bound to a specific interface or all interfaces. 7652 HTTP TCP event listener Binds to the LAN address. May be changed with advanced config i2np.upnp.HTTPPort=nnnn. May be disabled on confignet.7653 UPnP SSDP UDP search response listener Binds to the LAN address. May be changed with advanced config i2np.upnp.SSDPPort=nnnn. May be disabled on confignet.7654 I2P Client Protocol port Used by client apps. May be changed to a different port on configclients but this is not recommended. May be to bind to a different interface or all interfaces, or disabled, on configclients. 7655 UDP for SAM bridge A higher level socket API for clients Only opened when a SAM V3 client requests a UDP session. May be enabled/disabled on configclients. May be changed in the clients.configfile with the SAM command line optionsam.udp.port=nnnn.7656 SAM bridge A higher level socket API for clients Disabled by default for new installs as of release 0.6.5. May be enabled/disabled on configclients. May be changed in the clients.configfile.7657 Your router console May be disabled in the clients.configfile. May also be configured to be bound to a specific interface or all interfaces in that file.7658 Your I2P Site May be disabled in the clients.configfile. May also be configured to be bound to a specific interface or all interfaces in thejetty.xmlfile.7659 Outgoing mail to smtp.postman.i2p Puede desactivarse o modificarse en la página i2ptunnel de la consola del router. También puede configurarse para que esté vinculado a una interfaz específica o a todas las interfaces. 7660 Incoming mail from pop3.postman.i2p Puede desactivarse o modificarse en la página i2ptunnel de la consola del router. También puede configurarse para que esté vinculado a una interfaz específica o a todas las interfaces. 7670 (8998) gitssh.idk.i2p git over ssh This used to be port 8998 for monotone. Elder installations may still have that and not this one. May be disabled or changed on the i2ptunnel page in the router console. May also be configured to be bound to a specific interface or all interfaces. 31000 Local connection to the wrapper control channel port Outbound to 32000 only, does not listen on this port. Starts at 31000 and will increment until 31999 looking for a free port. To change, see the wrapper documentation. For more information see below. 32000 Local control channel for the service wrapper To change, see the wrapper documentation. For more information see below.
Los puertos locales de I2P y los puertos de I2PTunnel no necesitan ser accesibles desde máquinas remotas, pero *deberían* ser accesibles localmente. Además puede crear también puertos adicionales para instancias I2PTunnel vía http://localhost:7657/i2ptunnel/ (y a su vez, necesitará permitir en su cortafuegos el acceso local, pero no remoto, a no ser que lo desee así).
Resumiendo, nada necesita ser accesible por pares remotos que no hayan sido solicitados, pero, si puede configurar su NAT/cortafuegos para permitir conexiones de entrada UDP y TCP hacia los puertos de escucha de salida, tendrá mejor rendimiento. También necesitará ser capaz de enviar paquetes UDP de salida a pares remotos arbitrarios ( bloqueando IPs aleatoriamente con cosas como PeerGuardian solo le perjudica a usted - no lo haga).
Me faltan muchos anfitriones en mi libreta de direcciones. ¿Cuáles son algunos buenos enlaces de suscripción?
Esta pregunta puede responderse en 3 partes:
- Mi router muestra a menudo un mensaje que dice "Website Not Found In Address Book", ¿por qué veo este mensaje?
Human-readable addresses such as http://website.i2p are references to a long, random string known as a destination. These references are registered and stored at address book services such as stats.i2p, which is run by zzz. You will often encounter a "b32" address. A "b32" is a hash (specifically, a SHA256 hash) of the destination. This hash is appended with ".b32.i2p" and serves as a convenient way to link to your hidden service, without requiring any registration on an address book service.
It is possible to add subscriptions to your router's configuration which may reduce the frequency of these messages.
- What is an address book subscription?
This is a list of files hosted on various I2P websites each of which contain a list of I2P hosts and their associated destinations.
The address book is located at http://localhost:7657/dns where further information can be found.
- What are some good address book subscription links?
You may try the following:
¿Cómo puedo acceder a la consola web desde máquinas remotas y cómo la protejo con contraseña?
For security purposes, the router's admin console by default only listens for connections on the local interface. There are two methods for accessing the console remotely:
- SSH Tunnel
- Configuring your console to be available on a Public IP address with a username & password
These are detailed below:
- SSH Tunnel
If you are running a Unix-like Operating System, this is the easiest method for remotely accessing your I2P console. (Note: SSH server software is available for systems running Windows, for example https://github.com/PowerShell/Win32-OpenSSH)
Once you have configured SSH access to your system, the '-L' flag is passed to SSH with appropriate arguments - for example:ssh -L 7657:localhost:7657 (System_IP)ssh -NL 7657:localhost:7657 (System_IP) - Configuring your console to be available on a Public IP address with a username & password
- Open
~/.i2p/clients.configand replaceclientApp.0.args=7657 ::1,127.0.0.1 ./webapps/clientApp.0.args=7657 ::1,127.0.0.1,(System_IP) ./webapps/ - Go to http://localhost:7657/configui and add a console username and password if desired - Adding a username & password is highly recommended to secure your I2P console from tampering, which could lead to de-anonymization.
- Go to http://localhost:7657/index and hit "Graceful restart", which restarts the JVM and reloads the client applications
http://(System_IP):7657and you will be prompted for the username and password you specified in step 2 above if your browser supports the authentication popup.
NOTE: You can specify 0.0.0.0 in the above configuration. This specifies an interface, not a network or netmask. 0.0.0.0 means "bind to all interfaces", so it can be reachable on 127.0.0.1:7657 as well as any LAN/WAN IP. Be careful when using this option as the console will be available on ALL addresses configured on your system. - Open
¿Cómo puedo usar aplicaciones desde máquinas remotas?
Please see the previous answer for instructions on using SSH Port Forwarding, and also see this page in your console: http://localhost:7657/configi2cp
¿Es posible usar I2P como un proxy SOCKS?
The SOCKS proxy has been functional since release 0.7.1. SOCKS 4/4a/5 are supported. I2P does not have a SOCKS outproxy so it is limited to use within I2P only.
Many applications leak sensitive information that could identify you on the Internet and this is a risk that one should be aware of when using the I2P SOCKS proxy. I2P only filters connection data, but if the program you intend to run sends this information as content, I2P has no way to protect your anonymity. For example, some mail applications will send the IP address of the machine they are running on to a mail server. There is no way for I2P to filter this, thus using I2P to 'socksify' existing applications is possible, but extremely dangerous.
Si aún así desea mas información sobre el proxy socks, hay algunas sugerencias útiles en la web de socks
¿Cómo accedo al IRC, Bittorrent u otros servicios en la Internet regular?
Unless an outproxy has been specifically set up for the service you want to connect to, this cannot be done. There are only three types of outproxies running right now: HTTP, HTTPS, and email. Note that there is no SOCKS outproxy. If this type of service is required, we recommend that you use Tor. Please be aware that the Tor project recommends against using BitTorrent over Tor, as there are serious anonymity-related issues associated with doing so.
Privacy and Safety
¿Es mi router un "nodo de salida" a la Internet regular? No quiero que lo sea.
No. Unlike Tor, "exit nodes" - or "outproxies" as they are referred to on the I2P network - are not an inherent part of the network. Only volunteers who specifically set up and run separate applications will relay traffic to the regular Internet. There are very, very few of these. By default, I2P's HTTP Proxy (configured to run on port 4444) includes a single outproxy: false.i2p. This is run on a voluntary basis by Meeh. There is an outproxy guide available on our forums, if you would like to learn more about running an outproxy.
¿Es seguro utilizar I2P?
Before you use I2P, use Basic Computer Hygiene Always! Apply your OS vendor provided software updates in a prompt manner. Be aware of the state of your firewall and anti-virus status if you use one. Always get your software from authentic sources.
I2P strives to be safe in it's default configuration for all users.
It may be dangerous to use I2P in what the project calls "Strict Countries" where the law may not be clear on anonymizing software and where risks are judged to be fairly high. Most I2P peers are not in those strict countries and the ones that are, are placed in "Hidden Mode" where they interact with the rest of the network in more limited ways, so that they are less visible to network observers.
Veo las direcciones IP de todos los demás nodos I2P en la consola del router. ¿Significa eso que mi dirección IP es visible por los demás?
Yes, and this is how a fully distributed peer-to-peer network works. Every node participates in routing packets for others, so your IP address must be known to establish connections.
While the fact that your computer runs I2P is public, nobody can see your activities in it. You can't say if a user behind this IP address is sharing files, hosting a website, doing research or just running a node to contribute bandwidth to the project.
¿Es fácil detectar el uso de I2P analizando el tráfico de red?
It can be deduced that somebody is using the I2P network with some reliability, but it is a little difficult to know for sure. The most reliable way to know for sure would be to have a computer with a fairly stable IP address that you suspect is an I2P user, and a bunch of computers you control on different networks all running I2P. When one of them connects to your suspected computer, you will be able to see their I2P router in the netDB. This might take time, and it might never happen. You could also try blocking all obfuscated traffic on a particular network until you're sure every I2P router on that network has lost all of it's peers. At that point, they'll reach out to reseed servers to get more peers, which a network administrator can probably observe.
¿Es seguro usar un proxy de salida de I2P a Internet?
I2P does not encrypt the Internet, neither does Tor - for example, through Transport Layer Security (TLS). I2P and Tor both aim to transport your traffic as-is securely and anonymously over the corresponding network, to its destination. Any unencrypted traffic generated at your system will arrive at the outproxy (on I2P) or the exit node (on Tor) as unencrypted traffic. This means that you are vulnerable to snooping by the outproxy operators. One way to protect your outproxy traffic against this is to ensure that any traffic that will be handled by the outproxy is encrypted with TLS.
For more information, you may read the Tor FAQ's answer to this question: https://www.torproject.org/docs/faq#CanExitNodesEavesdrop
In addition, you may be vulnerable to collusion between the outproxy operator and operators of other I2P services, if you use the same tunnels ("shared clients"). There is additional discussion about this on zzz.i2p. This discussion has been mirrored on our forums as well.
Ultimately, this is a question that only you can answer because the correct answer depends on your browsing behaviour, your threat model, and how much you choose to trust the outproxy operator.
¿Qué pasa con los ataques de "Desanonimización"?
Reducing anonymity is typically done by A) identifying characteristics that are consistent across anonymous identities or B) identifying ephemeral characteristics of repeated connections. We say "reducing" anonymity because many of these characteristics are shared by many of our users, making these anonymity "sets," the smaller the anonymity set and the more small sets you belong to, the more brittle your anonymity.
Attacks on I2P in the past have relied on correlating NetDB storage and verification, by randomizing the delay between storage and verification, we reduce the consistency with which that verification can be linked to I2P activity, thereby limiting the utility of that data point.
Attacks on software configured to work with I2P are out of scope for I2P to solve. When browsing I2P or hosting I2P services, it's is the responsibility of the user to consider their threat model. Browsers are particularly problematic due to fingerprinting attacks, and the wide variety of information that can be gleaned from them. Using a standardized browsing profile is thought to help mitigate the impact of fingerprinting.
Reseeds
Mi router ha estado activo durante varios minutos y aún tiene ninguna o muy pocas conexiones
New installations of I2P carry out the reseeding process automatically, as well as when the number of known peers falls to a drastically low value. If you need to carry out a reseed of your router, please see the reseed instructions.
¿Cómo resiembro ('reseed') manualmente?
An I2P router only needs to be seeded once, to join the network for the first time. Reseeding involves fetching multiple "RouterInfo" files (bundled into a signed zip-file) from at least two predefined server URLs picked from a volunteer-run group of non-private internet HTTPS servers.
Un síntoma típico de un resembrado fallido es el indicador "Conocidos" (a la izquierda de la barra lateral de la consola del router I2P) mostrando un valor muy pequeño (a menudo menor que 5) que no se incrementa. Esto puede ocurrir, entre otras cosas, si su cortafuegos (firewall) local limita el tráfico saliente o si la petición de resembrado está bloqueada por completo.
Si está atrapado detrás de un cortafuegos o filtro de su proveedor de Internet (ISP), puede usar el siguiente método manual (solución técnica no-automatizada) para unirse a la red I2P.
Desde la versión 0.9.33, también puede configurar su router I2P para resembrar a través de proxy. Vaya a http://localhost:7657/configreseed y configure el tipo de proxy, nombre de servidor, y puerto.
Unirse a la red I2P usando un fichero de resembrado
Por favor, contacte con un amigo de conocida confianza que tenga un router I2P en ejecución, y pídale ayuda con el resembrado de su router I2P. Pídale que le envíe un fichero de resembrado exportado desde su router I2P en ejecución. Es vital que el fichero sea intercambiado a través de un canal seguro, ej. cifrado para evitar alteraciones externas (firma PGP, cifrado y verificado con una clave pública de confianza). El propio fichero no está firmado, así que, por favor, sólo acepte ficheros de amigos de conocida confianza. Nunca importe un fichero de resembrado si no puede verificar su procedencia.
Para importar el fichero i2preseed.zip recibido a su router I2P local:
- Vaya a http://localhost:7657/configreseed
- Bajo "Resembrado manual desde fichero" pulse "Examinar..."
- Seleccione el fichero i2preseed.zip
- Pulse "Resembrar desde fichero"
Compruebe el registro (log) para el siguiente mensaje:
Reseed got 100 router infos from file with 0 errors
Compartir un fichero de resembrado
Para amigos de confianza puede usar su router I2P local para brindarles un arranque asistido:
- Vaya a http://localhost:7657/configreseed
- Bajo "Crear Fichero de Resembrado" pulse "Crear fichero de resembrado"
- Enviar de forma segura el fichero i2preseed.zip a un amigo
¡No revele este fichero a usuarios desconocidos en ningún caso, ya que contiene datos privados sensibles (100 RouterInfo) de su propio router I2P! Para proteger su anonimato: puede esperar unas pocas horas/días antes de compartir el fichero con su amigo de confianza. También es aconsejable usar este procedimiento con moderación (< 2 veces por semana).
Directrices generales para el resembrado manual de I2P
- ¡No publique abiertamente el fichero de resembrado (clearnet) ni comparta estos ficheros con un amigo de un amigo (darknet)!
- ¡Este fichero sólo se debe usar para un número muy limitado de amigos (<3)!
- ¡El fichero sólo es válido unos pocos días (< 20)!
Internet Access/Performance
No puedo acceder a la Internet regular a través de I2P.
I2P is primarily not intended, nor designed, to be used as a proxy to the regular internet. With that said, there are services which are provided by volunteers that act as proxies to non-private internet based content - these are referred to as "outproxies" on the I2P network. There is an outproxy configured by default in I2P's HTTP client tunnel - false.i2p. While this service does currently exist, there is no guarantee that it will always be there as it is not an official service provided by the I2P project. If your main requirement from an anonymous network is the ability to access non-private internet resources, we would recommend using Tor.
No puedo acceder a sitios https:// o ftp:// a través de I2P.
- HTTPS
Within I2P, there is no requirement to use HTTPS. All traffic is encrypted end-to-end, any further encryption, e.g. with the use of HTTPS, doesn't create any further anonymity-related benefits. However, if one would like to use HTTPS or has a requirement to do so, the existing default I2P HTTP Proxy has support for HTTPS traffic. Any hidden service operator would have to specifically set up and enable HTTPS access. - FTP
El FTP no es compatible por razones técnicas. No existen "outproxies" FTP a Internet, ni siquiera es posible instalarlos. Cualquier otro tipo de outproxy puede funcionar si se configura con un túnel estándar. Si desea configurar algún tipo de outproxy, investigue cuidadosamente los riesgos potenciales. La comunidad I2P puede o no ayudarle con los aspectos técnicos, no dude en preguntar. Como ya se ha explicado en varias ocasiones, cualquier outproxy existente no es una parte central de la red. Son servicios gestionados por particulares y pueden estar operativos o no en un momento dado.
Mi router está utilizando una gran cantidad de CPU, ¿qué puedo hacer al respecto?
Hay muchas causas posibles para un elevado uso de la CPU. Aquí tiene una lista para su comprobación:
-
Java Runtime Environment
Try to use either OpenJDK or Sun/Oracle Java if it's available for your system. You can check which version of java you have installed by typingjava -versionat a command/shell prompt. Performance tends to suffer with other implementations of java. -
Aplicaciones de intercambio de archivos, como BitTorrent
¿Está ejecutando un cliente Bittorrent sobre I2P? Intente reducir el número de torrents, los límites de ancho de banda, o pruebe a apagarlo completamente a ver si eso ayuda. -
Ajustes de gran ancho de banda
¿Están sus límites de ancho de banda configurados demasiado altos? Es posible que pase demasiado tráfico a través de su router I2P y esté saturado. Intente reducir el porcentaje de ancho de banda compartido en la página de configuración. -
Versión de I2P
Asegúrese de usar la última versión de I2P para beneficiarse de las mejoras de rendimiento y la solución de errores. -
Asignación de memoria
Has enough memory been set aside for use by I2P? Look at the memory graph on the graphs page to see if the memory usage is "pegged"—the JVM is spending most of its time in garbage collection. Increase the settingwrapper.java.maxmemoryin the filewrapper.config. -
Bursts of high-usage vs. constant 100% usage
¿El uso de la CPU es simplemente mayor de lo que te gustaría, o está fijado en 100% durante mucho tiempo? Si es así, podría tratarse de un error. Busca pistas en los registros. -
Java-related
Puede que esté usando la librería BigInteger en vez de la versión nativa, especialmente si lo ejecuta en un sistema o hardware nuevo o inusual (OpenSolaris, mipsel, etc). Visite la web de jbigi que incluye instrucciones para el diagnóstico, compilado y métodos de testeo. -
Túneles participantes
If your native jbigi library is working fine, the biggest user of CPU may be routing traffic for participating tunnels. This uses CPU because at each hop a layer of encryption must be decoded. You can limit participating traffic in two ways - by reducing the share bandwidth on the confignet page, or by setting router.maxParticipatingTunnels=nnn on the configadvanced page.
Mi router tiene muy pocos pares ('peers') activos, ¿está bien esto?
If your router has 10 or more active peers, everything is fine. The router should maintain connections to a few peers at all times. The best way to stay "better-connected" to the network is to share more bandwidth. The amount of bandwidth that is shared by the router can be changed on the configuration page: http://localhost:7657/config
¡Mis pares activos / pares conocidos / túneles participantes / conexiones / ancho de banda, varían dramáticamente a lo largo del tiempo! ¿Está mal algo?
No, no pasa nada. Es un comportamiento normal. Todos los routers se ajustan dinámicamente a las condiciones y demandas cambiantes de la red. Los routers se conectan y desconectan dependiendo de si el sistema en el que están instalados está operativo o no, así como de si hay una conexión de red disponible. El router actualiza constantemente su base de datos de red local. Los túneles en los que participa su router expiran cada 10 minutos y pueden o no ser reconstruidos a través de su router.
¿Qué hace que las descargas, los torrents, la navegación web y todo lo demás sea más lento en I2P en comparación con Internet normal?
El cifrado y el encaminamiento dentro de la red I2P añaden una cantidad considerable de sobrecarga y limitan el ancho de banda. Podemos intentar aclararlo con ayuda de un diagrama:
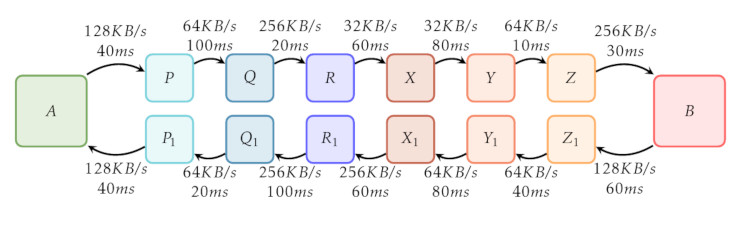
En este diagrama se muestra la ruta que sigue el tráfico I2P en su viaje por la red. El enrutador I2P de un usuario está representado por la casilla "A" y un servicio oculto I2P (por ejemplo, el sitio web http://stats.i2p) por la casilla "B". Tanto el cliente como el servidor utilizan túneles de 3 saltos, representados por las casillas "P", "Q", "R", "X", "Y", "Z", "P_1", "Q_1", "R'_1, "X_1", "Y_1" y "Z_1".
Las casillas "P", "Q" y "R" representan un túnel de salida para A, mientras que las casillas "X_1", "Y_1" y "Z_1" representan un túnel de salida para "B". Del mismo modo, las casillas "X", "Y" y "Z" representan un túnel de entrada para "B", mientras que las casillas "P_1", "Q_1" y "R_1" representan un túnel de entrada para "A". Las flechas entre las casillas indican el sentido del tráfico. El texto encima y debajo de las flechas muestra ejemplos de ancho de banda entre un par de saltos y ejemplos de latencia.
Cuando tanto el cliente como el servidor utilizan túneles de 3 saltos, un total de otros 12 enrutadores I2P participan en la retransmisión del tráfico. 6 peers retransmiten el tráfico del cliente al servidor, que se divide en un túnel de salida de 3 saltos desde "A" ("P", "Q", "R") y un túnel de entrada de 3 saltos hacia "B" ("X", "Y", "Z"). Del mismo modo, 6 pares retransmiten el tráfico desde el servidor hasta el cliente.
En primer lugar, podemos considerar la latencia: el tiempo que tarda una solicitud de un cliente en atravesar la red I2P, llegar al servidor y volver al cliente. Sumando todas las latencias vemos que:
40 + 100 + 20 + 60 + 80 + 10 + 30 ms (client to server)
+ 60 + 40 + 80 + 60 + 100 + 20 + 40 ms (server to client)
-----------------------------------
TOTAL: 740 ms
En nuestro ejemplo, el tiempo total de ida y vuelta asciende a 740 ms, mucho más de lo que se tarda normalmente en navegar por sitios web normales.
Second, we can consider available bandwidth. This is determined through the slowest link between hops from the client and server as well as when traffic is being transmitted by the server to the client. For traffic going from the client to the server, we see that the available bandwidth in our example between hops 'R' & 'X' as well as hops 'X' & 'Y' is 32 KB/s. Despite higher available bandwidth between the other hops, these hops will act as a bottleneck and will limit the maximum available bandwidth for traffic from 'A' to 'B' at 32 KB/s. Similarly, tracing the path from server to client shows that there is maximum bandwidth of 64 KB/s - between hops 'Z_1' & 'Y_1, 'Y_1' & 'X_1' and 'Q_1' & 'P_1'.
We recommend increasing your bandwidth limits. This helps the network by increasing the amount of available bandwidth which will in turn improve your I2P experience. Bandwidth settings are located on the http://localhost:7657/config page. Please be aware of your internet connection's limits as determined by your ISP, and adjust your settings accordingly.
También recomendamos establecer una cantidad suficiente de ancho de banda compartido - esto permite que los túneles participantes sean enrutados a través de su router I2P. Permitir el tráfico participante mantiene su router bien integrado en la red y mejora sus velocidades de transferencia.
I2P es un trabajo en curso. Muchas mejoras y arreglos están siendo implementadas, y generalmente usando la última versión mejorará el rendimiento. Si no la tiene, instale la última versión.
Creo que he encontrado un error, ¿dónde puedo reportarlo?
Puedes informar de cualquier error/problema que encuentres en nuestro bugtracker, que está disponible tanto en Internet no privado como en I2P. Tenemos un foro de debate, también disponible en I2P y en Internet no privado. También puedes unirte a nuestro canal de IRC: ya sea a través de nuestra red IRC, IRC2P, o en Freenode.
- Our Bugtracker:
- Internet no privado: https://i2pgit.org/I2P_Developers/i2p.i2p/issues
- En I2P: http://git.idk.i2p/I2P_Developers/i2p.i2p/issues
- Nuestros foros: i2pforum.net
- You may paste any interesting logs to a paste service such as the non-private internet services listed on the PrivateBin Wiki, or an I2P paste service such as this PrivateBin instance or this Javascript-free paste service and follow up on IRC in #i2p
- Únete a #i2p-dev Discute con los desarrolladores en IRC
Please include relevant information from the router logs page which is available at: http://127.0.0.1:7657/logs. We request that you share all of the text under the 'I2P Version and Running Environment' section as well as any errors or warnings displayed in the various logs displayed on the page.
¡Tengo una pregunta!
Great! Find us on IRC:
- on
irc.freenode.netchannel#i2p - on
IRC2Pchannel#i2p


























